Our Solutions

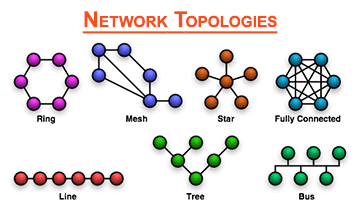
Some are our Key solutions are :
- Network infrastructure solutions
- Structure Cabling – UTP & OFC
- Campus Area Networking Solutions
- Point to Point wireless solutions
- Point to Multipoint wireless solutions
- Active device solutions
- VLAN Solutions
- User access control solutions
- Network load balancing solutions
- Door access solutions
- Time and Attendance solutions
Laya Tech Private Ltd. is engaged in the design, marketing of hardware and software used in connecting all computer associated equipment in the business and domestic environment, such as personal computers (PCs), workstations, printers, scanners, fax and vending machines to local area networks (LANs), wide area networks (WANs) and the Internet. We also engaged in security and access control devices for connection to computer networks, as well as security management software for use within organizations and enterprise networks.
Twisted pair wire is the most widely used medium for all telecommunication. Twisted-pair cabling consist of copper wires that are twisted into pairs. Ordinary telephone wires consist of two insulated copper wires twisted into pairs. Computer network cabling (wired Ethernet as defined by IEEE 802.3) consists of 4 pairs of copper cabling that can be utilized for both voice and data transmission. The use of two wires twisted together helps to reduce crosstalk and electromagnetic induction. The transmission speed ranges from 2 million bits per second to 10 billion bits per second. Twisted pair cabling comes in two forms: unshielded twisted pair (UTP) and shielded twisted-pair (STP). Each form comes in several category ratings, designed for use in various scenarios.
An optical fiber is a glass fiber. It uses pulses of light to transmit data. Some advantages of optical fibers over metal wires are very low transmission loss and immunity from electrical interference. Optical fibers can simultaneously carry multiple wavelengths of light which greatly increases the rate that data can be sent, and helps enable data rates of up to trillions of bits per second. Optic fibers can be used for long runs of cable carrying very high data rates, and are used for undersea cables to interconnect continents.
Radio and spread spectrum technologies – Wireless local area networks use a high-frequency radio technology similar to digital cellular and a low-frequency radio technology. Wireless LANs use spread spectrum technology to enable communication between multiple devices in a limited area. IEEE 802.11 defines a common flavor of open-standards wireless radio-wave technology known as Wifi.
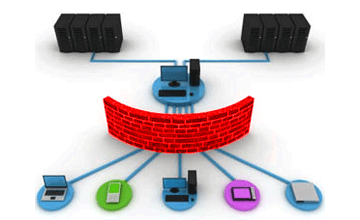
Some are our Key solutions are :
- Unified Threat Management Solutions
- Data Leak Prevention Solutions
- Intrusion Prevention System
- Intrusion Detection System
- Two Factor Authentication Solutions
- Anti Spam Solutions
- Anti Virus Solutions
- Proxy Server Solutions
- Link Load Balancer Solutions
- Application Load Balancer Solutions
- Network Access Control (NAC) Solutions
- WAN Optimizer Solutions
Cyber threats, today, are more complex and more sophisticated than ever before. Cyber attacks pose risks to homeland security and nation’s economy that have far-reaching impact and implications that may not currently be realized. We need the best and the brightest cyber experts to support the mission to protect and defend the country against cyber warfare.
Global economic and IT security environment presents organizations with the constant challenge of increasing operational efficiency while also managing critical risk, protecting vital information, demonstrating compliance with regulatory and industry standards.
The dramatic increase of insider threats to sensitive data, explosive growth of malware and targeted attacks and strict enforcement of security and operations standards mean organizations must focus on TCO and effective risk management while still investing in their strategic security initiatives.
Laya Tech Private Ltd. provides world-class cyber security, information security, and cyber intelligence services and solutions that enable clients to detect and defend against cyber threats to their critical network infrastructures, and establish network stability and resilience that will endure. The result is improved security, risk mitigation and audit readiness at a lower investment of operational resources, time and money.

Some are our Key solutions are :
- Server designing solutions
- Storage solutions
- Virtualization solutions
- Disk / Diskless solutions
- Active Directory solutions
- E-Mail solutions
The world of information technology (IT) changing rapidly, traditional approaches to solving infrastructure problems are inadequate. The vision for this new era of IT is to provide consistent platform for infrastructure, apps, and data with server,storage and virtualization solution, you gain an enterprise-grade platform to cost-effectively optimize your business.
To compete in today’s economy you need an infrastructure that is agile enough to change as rapidly as your business strategies change. That flexibility requires a high level of integration.
Servers often provide essential services across a network, either to private users inside a large organization or to public users via the Internet. Typical computing servers areApplication server,Catalog server,Communications server, Computeserver,Database server, Fax server,Fileserver, Game server, Home server, Mail server, Mobile Server, Name server or DNS, Print server, Proxy server, Sound server, stand-alone server, web server.
Organizations today need to manage, process, and store huge amounts of complex data. Storage can help you get control of your data, take on even the biggest business challenges, and turn data-driven insight into action quickly.
Organizations today need to manage, process, and store huge amounts of complex data. Storage can help you get control of your data, take on even the biggest business challenges, and turn data-driven insight into action quickly.
We must remember here is that efforts to maximize the server utilization is limited by the number of incoming server requests. So, if you have done your best to ensure that a server spends a good fraction of the time servicing requests, this is only as much as the number of requests the server receives at any point of time. So, how exactly do we eliminate this wastage and thereby maximize the profits then the answer to this problem lies with virtualization.
In computing, virtualization means to create a virtual version of adevice or resource, such as a server, storage device, network or even an operating system where the framework divides the resource into one or more execution environments. Even something as simple as partitioning a hard drive is considered virtualization because you take one drive and partition it to create two separate hard drives. Devices, applications and human users are able to interact with the virtual resource as if it were a real single logical resource. The term virtualization has become somewhat of a buzzword, and as a result the term is now associated with a number of computing technologies
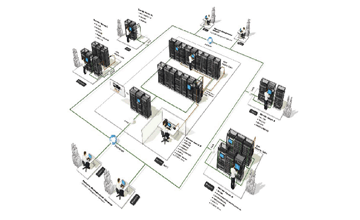
Some are our Key solutions are :
- Design Solutions
- Civil solutions
- Structural solutions
- Electrical solutions
- Mechanical solutions
- Security solutions
- Data cabling solutions
- Interior solutions
As the demands on IT departments increase, managing the expertise and resources required to support the entire IT delivery ecosystem is becoming more difficult and more expensive for mid-size organizations. There is much more to building and operating a data center than filling a room up with servers. Every aspect of a soft Layer data center—from power density and redundancy, to capacity and cooling, and location and accessibility—is designed to guarantee its security, resiliency, and efficiency. The massive growth of digital data and the challenges of how to secure, manage and store that data is only increasing, with some companies that manage their own internal data centers running out of space, power or cooling capacity.
The decision to consolidate, move and/or expand your data center is an important part of your IT infrastructure strategy, and it should include assessing hard and soft costs associated with leasing data center space vs. owning. Risk tolerance and redundancy requirements are also key factors to consider. Many companies find that offsite collocation offers an attractive alternative to owning and maintaining their own data centers. They benefit by outsourcing the management and maintenance of a data center infrastructure, while retaining the access and control over their mission-critical information and business applications.
Key note points to have DC to Reduced IT Infrastructure, Management Costs, Power Capacity, Redundancy, Reliability, Uptime, Robust, Affordable Bandwidth, 24/7 Support, Security, Data Protection, Business Continuity and Disaster Recovery.
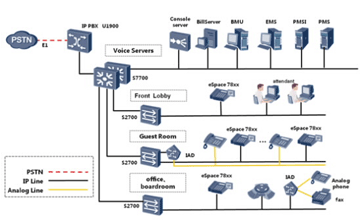
Some are our Key solutions are :
- IP PBX
- SIP Solutions
- Video conferencing solutions
- Multipoint videoconferencing solutions
- Cloud-based video conferencing solutions
- VOIP Solutions
- IP Phones solutions
- Board Room solutions
- Tele presence solutions
The main challenges of determining the right enterprise mobility strategy for an organization is to relate the available mobile IT to the overall purpose of the work conducted, to determine how closely the business process should be aligned to the mobile IT, and how to support mobile workers when they are using these devices in the workplace.
Unified communications is the integration of real-time communication services such as instant messaging (chat), presence information, telephony (including IP telephony), video conferencing, data sharing (including web connected electronic whiteboards interactive whiteboards), call control and speech recognition with non-real-time communication services such as unified messaging(integrated voicemail, e-mail, SMS and fax). Unified Communication is not necessarily a single product, but a set of products that provides a consistent unified user-interface and user-experience across multiple devices and media-types.
Unified Communication allows an individual to send a message on one medium, and receive the same communication on another medium. For example, one can receive a voicemail message and choose to access it through e-mail or a cell phone. If the sender is online according to the presence information and currently accepts calls, the response can be sent immediately through text chat or video call. Otherwise, it may be sent as a non-real-time message that can be accessed through a variety of media.
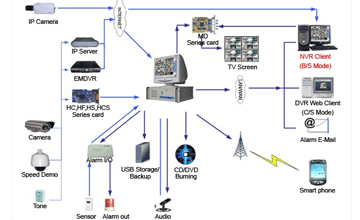
Some are our Key solutions are :
- End to End IP camera surveillance solution
- Securing indoor and outdoor facilities
- Reliable detection and completion
- Network Video recording (NVR)
Camera system is being widely employed as a security system for surveillance in offices as well as homes. It is used for monitoring purposes to keep a close vigil. Not only in closed or private places; CCTV camera system extends as a security system in public and crowded places like Company production area, offices , education institutes, hospital, traffic, intersections, malls, shops, etc. It helps to detect crimes, maintain records, and protect employees, evidence in lawsuits.
An Internet protocol camera, or IP camera, is a type of digital video camera commonly employed for surveillance, and which unlike analog closed circuit television (CCTV) cameras can send and receive data via a computer network and the Internet. Although most cameras that do this are webcams, the term IP camera is usually applied only to those used for surveillance.
There are two kinds of IP cameras:
Centralized IP cameras, which require a central Network Video Recorder (NVR) to handle the recording, video and alarm management.
Decentralized IP cameras, which do not require a central Network Video Recorder (NVR), as the cameras have recording function built-in and can thus record directly to local storage media, such as flash drives and hard disk drives or to standard network attached storage.
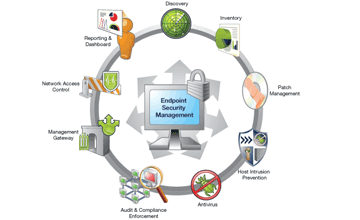
Some are our Key solutions are :
- Data backup solutions
- Antivirus solutions
- Data leak prevention solutions
- Device control solutions
- Asset management solutions
- Single sign on solutions
- Patch management solutions
- Application management solutions
The design and implementation of security solutions for even moderately complex enterprises is an extremely difficult undertaking. In realistic environments, the enterprise being protected, the value distribution within the enterprise and the security threats are continuously evolving and, therefore, traditional security designs can result in solutions that, over time, are protecting the wrong assets against the wrong threats.
Practical security solution design, therefore, need to accommodate that the nature of the problem that they initially need to solve is imperfectly known and that the problem will continue to evolve over the life of the system.
Effective security solutions that provide long-term utility in this complex and evolving environment, therefore, require a highly structured and disciplined design approach. At the same time, it is not practical to approach every security challenge with a solution that is developed from first principles on the other hand, is known to be cost-effective and poses low implementation risk.
Endpoint, therefore, is a critical element in the design process for the complex solutions required to meet the security challenges of today – and tomorrow. It is also, however, the core backbone of the implemented solution itself.
Endpoint, from Laya Tech Private Ltd., has been developed as a solution framework that enables the development of sophisticated security solutions in a stable technical context that enables rapid implementation of cost-effective structures that can be adapted in situ to meet specific requirements and which can continue to evolve as requirements and technology change.